A9 Maps discontinued
As of September 29th, 2006, A9 Maps including Block View has been discontinued. This of course means that the mashup described below is no longer working and I have removed the web service from my site. You are still wecome to read about, and download the code if you find it useful.
A9 Block View
Some time ago, Amazon/A9 came out with their new map service which sported a pretty cool feature, the Block View. They have basically driven around the streets of a number of major US cities, continuously taking pictures of both sides of the street and logging GPS coordinates together with the images. When you go to their maps/local service and search for a business or an address, you get to see an actual picture of the street at that spot together with the map. Very neat.
Example of A9 Block View Images from New York
Block View and Google Earth
I found a post on the Google Earth community site that asked if anyone had managed to do a mashup of A9 Block View and Google Earth. I must admit I had not heard about this cool feature before, so I decided to check it out. The post was almost a year old and though there were a couple of answers, no one seemed to have actually built the mashup.I had an idea of a simple setup where I would display a placemark in the middle of the bounding box from Google Earth and if the user clicked it, display the image from that location. There were two issues though:
- How to get the correct image from the A9 server.
- How to know when there was no image available for a location.
A9 inspection
I had hoped that A9 would use a scheme similar to Eniro, where you build a URL for an image with parameters specifying the location somehow. A quick inspection of the image URLs ruled that out though. The URLs seemed to be built using some kind of fingerprinting, a typical URL could look like this:http://images-yp.amazon.com/ImageServer/view/j_dX-YUVOIXKtt
Pw9Y96BAJzPhr1RHzJb-u_bHE-XFRRQlA98OZzXskz8LEyLdP282kYyY3RJ
mZ7No05GhqRtXkJNkgWpe2vUi5_q3MdXA2AIVeft_FLnLLMtx5HiXLfkafi
zwjcEdET0GJgfOwa7Q==
Not pretty...
OK, back to the drawing board. I called upon my old friend "View Page Source" and started wading through the JavaScript. It turned out A9 has a very nice XmlHttp interface with a lot of useful methods. There was for instance the promising method "blockview" which took a lat, long position as query parameters. I constructed a URL which seemed to fit the format and typed it into the address field in my browser and lo and behold, got a nice piece of XML in return! The format of the call is as follows:
maps.a9.com/-/maps/xService.jsp?
smykowski=blockview¢erLat=[lat]¢erLon=[lon]&numPanes=[npanes]
(line broken for readability)
lat and lon are of course the position you are interested in getting data for.
Some experimenting with the npanes parameter showed that it controlled how many consecutive images along the street was returned.
By the way, who is this Smykowski...? :)
A9 XML
The XML that is returned by the A9 server is very regular. It has only three types of elements, Hash, Scalar and Value. Hash and Scalar has always a name attribute, and every Scalar contains a Value sub element. Hash elements can nest. Example:
<Hash name="double-mint">
<Hash name="facing">
<Hash name="center">
<Scalar name="lat">
<Value>41.89293611111111</Value>
</Scalar>
<Scalar name="lon">
<Value>-87.62394444444445</Value>
</Scalar>
<Scalar name="dir">
<Value>354.8837549589973</Value>
</Scalar>
</Hash>
<Hash name="pan">
<Scalar name="fwdLat">
<Value>41.892977018457906</Value>
</Scalar>
<Scalar name="fwdLon">
<Value>-87.623948107019</Value>
</Scalar>
</Hash>
</Hash>
</Hash>
This example is only an extract of a real reply from the server, which is much longer.
Some experimenting gave that there were Hash sections named panes-n, where n=[0, npanes) which contained the desired image URLs for the corresponding location. It even gave URLs to the same image in three different resolutions. If there were no images available there were simply no such elements.
As long as we were inside the United States, there was also a Scalar with the name street-name giving the closest street for the location. We got that regardless if images were found ot not. If we ventured outside the US, we got an empty reply.
Code
With all these facts in place, coding the thing is fairly straight forward.- Get the call from Google Earth and extract the bounding box of the area the user is watching. Calculate its mid point.
- Build a call to the A9 XML server and ask for data on that location.
- Parse the returned XML and build a KML string that points out the images.
I have implemented this in C# in an ASP.NET page. You can download the code below. Some notes:
I am a lazy bum, so there is no real XML parsing in the code, I just use a bunch of regular expressions to dig out what I need (this is after all a hack).
There is some functionality in the code not described here, like getting a real street address if we find images. This is done by another call to the A9 server with a technique almost identical to the one described above.
The code builds a KML placemark with three thumbnail images from each side of the street. Each thumbnail is in turn a link to a larger image so if you click it , it will show up in the web panel.
Result
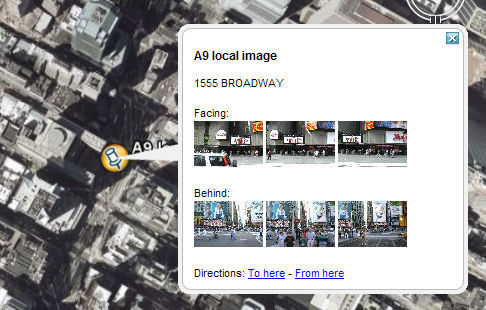
Resulting placemark at 1555 Brodway i New York
But wait, aren't we forgetting something...?
How do you actually use this?
Well, you grab the file above and install it on a web server that supports ASP.NET. Then you create the actual network link in Google Earth that points to that server. I will leave that as an exercise for the reader for now. Hint: Right click on "My Places" and select "Add"...
Ok, ok, just kidding... The zip-file contains an example of such a KML file that points to a service on this server. If you install the ASP.NET page on your own server, remember to change the link in the KML file as well.
Happy Hacking!